5. INTELLIGENCEIntelligence - sounds a funny occupation for a bunch of hippies? But to be really effective it's not just enough to hit sites and get away with it. You must also be aware of what's going on around you, and what those around you (mainly the police and government anti-terrorist bunch) are doing about you. Intelligence is primarily about three issues... Also, this type of work does not provide instant answers - you must assemble different pieces of the puzzle to produce the answer. So, in the normal course of events you would find out about something, take steps to discover more, and if you are lucky, come up with an answer which pre-empts the opposition. In relation to what other 'intelligence' operatives are doing about you, it's also a matter of developing ways of living and working which give as little information away as possible on your secretive hobby. For your information, following completion of this tome I might write a document specifically for techno-freaks who want to do some proper intelligence and encryption work of their own. Keep your eyes open! 5.1 Anti-surveillance measuresIf you are the type who stirs things in your community, political things, peace, environment or civil rights type things, chances are you will be on somebody's list. There are various bodies who 'monitor' the community... In the UK, the warrants granted to intercept post, or tap phones, are granted on an 'organisational wide' basis. Thus, when granting a warrant against CND for example, it would not only cover the CND head office, but also any person who worked or was an active member of the organisation. This is why Home Office figures are so misleading - they refer to the number of groups of people covered, not the actual number of intercepts. So, potentially all these people are watching you. What can you do about it? 5.1.1 Your phonePhone taps, especially for people who use phones a lot, are a good way to pick up information. As well as taping your voice conversations, with the appropriate equipment, private investigators as well as the 'official' government departments can monitor fax and computer/modem transmissions too. There is no way to prevent, or detect, any official (Government) telephone tap. Today, with digital telephone switching technology, government agencies do not even have to physically visit your exchange to set a tap on your phone - they just instruct their computer to tell BT's or Mercury's computers to redirect a copy of your phone conversations to their computer systems. Unofficial taps are another matter. Generally unofficial taps are physically connected to your phone line, either taking power from the line (in which case, the line will be cut and the device connected into the circuit) or picking up the phone signals by inductance (in which case the device will have a coil of wire around the phone line - with no physical connection - and it will have to have its own power supply). Those with direct connection will reduce the voltage on the telephone line, but voltages can vary so much anyway they are still difficult to detect unless you have very expensive equipment. The traditional image of official phone taps is a large tape machine which records when you pick your phone up. These machines produced hours of tape, which all had to be listened to costing lots of staff time and money. This meant tapping was only used where the results were guaranteed, or it was an absolute necessity to have continuous monitoring. Today, with computer technology, this is no longer the case. The phone tap plays into a computer. The computer is programmed with snippets of your voice speaking 'keywords' - for example "hit", "nuclear", "explosive", "bomb", etc. - gathered from previous phone recordings. When the conversation has been recorded, the computer digitally examines the playback looking for these words. If it finds a match then it keeps the recording for later use. This has made tapping easier, and thus more widespread. There is absolutely no way to defend yourself against phone tapping - you just have to work around the problem. Rather than organising things on the phone you have to do it in person, or invent a variable and confusing set of codewords to fool the listeners. If you have a computer things get easier - it is possible to send encrypted (scrambled) messages via a modem, or just on a floppy disk through the post. Even so, the growing power of computers means that unless you have a very good encryption program the code may be broken eventually. Mobile phones are another option - but make sure it is the 'digital' type which encrypts the call. Even then, this does not stop the Government eavesdropping on you because, via the phone company, they will have access to your code. Another practice used by various tappers, and widely used by the police and security services, is number logging. The authorities only have to have a warrant to actually 'listen' to the call - they can make a note of the numbers dialled from the premises without any control whatsoever. Also, now that exchanges are fully digital, they can also find out the number of people calling you. From this information it is possible to draw up a 'web' of your contacts and associates. Another tip - if someone suspicious phones you up, if you are on a digital exchange, dialling 1471 immediately after you finish the call will give you their number. If the voice tells you that, 'there is no number stored', this means that the number was withheld deliberately, that the person was ex-directory, that they were phoning from a non-digital exchange (pretty difficult thing to do these days) or that they were calling from a mobile phone. If for any reason you wish to withhold your number when dialling someone, simply dial 141 before you dial the number and the switching computer will not release your number to them. 5.1.2 Your mailUnless you leave your post in a box at the end of the drive (common in country areas) it is difficult for unofficial bodies to intercept your post. The government, the police or the security services can get a warrant to do so at any time. Not all your post will be searched. Those plastic packages marked 'sealed under licence' will not be searched - there is no need as no one apart from the sender can put stuff inside. Likewise identifiable communications from companies (normally identifiable by the franking machine mark) or the DHSS may not be searched. Hand-written envelopes, and anything which is not immediately identifiable will be. The techniques used to open your post are very good - it is often difficult to tell that it has been tampered with. I suspect that my post is intercepted (I wonder why - could it be the things I write?) and the only indication that there is something wrong is that packages sent at the same time from the same place take a day or so longer to get to me than it does to others in the same area as me. There is little you can do to prevent your post being read. The only easy solution is to write your letters on computer, encrypt them, and then send them on floppy disk through the post or if the recipient has an Internet connection email it to them. 5.1.3 Your homeThere are various ways to extract information from your home. Bugs are the simple and much hyped way, although there are others... Once they have an address they can use the measures outlined above to stake out your home and your phone. If you have a car they can illicitly get information on you via the DVLC, and increasingly information from the police national computer is finding its way into private hands. By sorting your rubbish they can find out where your bank account is. Having done that they can pose as, or pay, a loans company to get details about your credit worthiness. Again, by bribery and corruption, it is also possible to get your benefits details. Finally, by tracing your movements, logging incoming and outgoing call numbers, or watching your house, they can build up a comprehensive picture of your friends and associates. Of course, all the above relates primarily to private investigators or determined snoops - official authorities can do much more than this! 5.1.4 Your informationAny information you keep at your home is vulnerable. Some associates of mine have been 'burgled', and all the people were interested in was the information in their filing cabinets or on their floppy disks. You must be aware that if you keep any significant amount of data at home, especially where that data is an essential part of any campaigning activities, you are giving an open initiation to the 'opposition' to burgle or burn you home. A journalist friend working on defence related investigation a number of years ago gave me four basic principles for keeping information at home... The most important of these rules must be that you copy any useful information to your associates. This is good for two reasons. Firstly it keeps the data safe. Secondly, it encourages the sharing of data and resources which makes life a lot simpler for everyone involved. 5.2 Basic surveillance equipmentThe information above outlines what others can do to you to invade your privacy. If circumstances warrant, there may be times when you will want to invade the privacy of others. The following information should help. However, I would advise you to always consider how you do anything like this. Unless, if the situation were reversed, you could not justify taking the same actions - don't do it. 5.2.1 BugsIt is possible to see working bugs or kits advertised in many electrical hobbyists magazines. But realistically using these devices is another matter. Most bugs you see advertised work in or near the VHF broadcast band - 88MHz (megahertz) to 108MHz. This presents an obvious difficulty if your target tunes through the radio band one day and hears a conversation in the room next door! To be secure it is necessary to tune outside of the normal broadcast band - this means having the technical know-how to do this yourself, or paying £75 to £1000 for a radio which will pick up just about any frequency. Even then, if the target sweeps their home for bugs, or if they are a radio freak who has multiband receivers in their home/office, then they might find out anyway. Having got your bug, your receiver, utilising frequencies outside everyday broadcast bands, the next problem is locating the device. As noted above, your greatest problem will be finding a power source. Unless you can wire the thing into the mains, you will have to rely upon a finite amount of battery power. You will therefore have to select the most appropriate time to plant the device to get the best effect. It will also be necessary to gain access to the room you want to bug - potentially the flaw in the whole scheme. If you are bugging a site office such as a portakabin this can be easier - you can sneak up to the office overnight, drill a small hole in the wall or ceiling where it will not be seen, and poke the microphone through the hole. In more substantial premises, you are either going to have to break in (a bit obvious to your target) or get proficient in lock picking. There is another option - if the persons concerned are themselves using radio equipment to communicate, you could drop in on their communications using the appropriate type of receiver. When planting the device, unless you want to create an enormous fuss when it is eventually found, you have to consider how you will retrieve it. For example, it would be quite easy to bug a secret council meeting since the council chamber is open for most of the time - but what if the cleaner finds the device the next day? The next thing you have to consider is how you will monitor the device. The range of the average bug is about half a kilometre, if you're lucky. The presence of buildings, structures, and especially metal such as reinforced concrete will limit the range. You will have to find somewhere to sit and listen at the appropriate time where you will not be disturbed, or noticed. The other option is to plug the earphone/recording output from the receiver into some sort of dictaphone which will give you a couple of hours of recording time on one tape, or a device that has some sort of detection level system so that it only switches on when it picks up a noise. All in all, I think you have to be pretty desperate to use any sort of bug, mainly because of all the hassle involved in getting what may turn out to be completely useless information. 5.2.2 Phone tapsInterfering with people's phones is problematic. The slightest mistake and the line might develop a fault - in which case BT will be out and will track down your device in a matter of hours. There are basically two sorts of phone tap which are within the technical capability of the average electrical hobbyist - direct connection devices and induction taps. Direct connection devices are wired into the phone line, and draw power from it so removing the need for batteries. However, the half-kilometre range factor still applies and so you'll still have to find somewhere nearby to receive the signal. Again, kits can be illicitly bought through hobby magazines. Induction devices require that you wind a couple of hundred coils of wire around the phone line - and then amplify and transmit the signal. You can have higher powered transmitters because the device is not solely reliant on power from the phone line, but you have the problem of actually supplying the power to the device, much in the same way as a conventional bug. The problem about transmission frequency still applies - most of these devices are tuned to the 88-108MHz broadcast band. However, because the device can be connected anywhere along the phone line from the house to the exchange, they are easier to place and monitor, and will not be picked up when sweeping the house. However, there is (expensive) equipment available that can pick up directly connected devices. 5.2.3 Audio/recording devicesMy preferred way of working is a concealed dictaphone. You have the same problems about batteries and actually placing the thing, but you tend to get better results. Most modern models will also have 'voice activation' features so that it will only record when there is actually a noise to record. The only problem is that the price of a dictaphone is about five or seven times that of a bug (£50-£70, as opposed to £10 for a simple bug). Another option, rather than planting the dictaphone inside a building, is to fix a 'contact' microphone to a window, and plug the mike into a dictaphone. The contact mike picks up the vibration cause by noises in the room and sends them to the dictaphone. The only problem is that the mike also picks up bangs and bumps in the building, and an awful lot of wind noise. Finally, you could just drill a small hole through the wall of a building and then insert a micro-miniature microphone. The microphone has an amplifier mounted just behind it so that the signal can be sent many metres down a cable to a recorder - the device also receives its power back along the same cable. A similar design of a device is also very good for 'wiring up' a building using the mains trunking as the transmission system, with the microphones placed in the junction boxes/wall sockets. 5.2.4 Video/photographsThere are two requirements for good photographic observation - a high powered lens and a direct, clear view. A video camera is not the sort of thing that is normally use for unofficial eavesdropping because of the expense - although a concealed camera, activated by motion switches or pressure pads, is a good way to keep watch on your home for uninvited intruders while you are away. 5.3 Rubbish sortingA disgusting job, but one which produces a surprisingly large amount of useful information. Having identified your target you next find out where their dustbin is, and what day they put their rubbish out. Then, when no one is around, you remove it to sort for any interesting information, then return it later. Domestic targets can produce some - very messy - information, but commercial targets provide possibly the best source. This is because much of what they put out is paper, normally dealing with the business that is happening there and then. From experience, paperwork from people's homes tends to be sporadically put out, perhaps during the odd spring clean of a person's filing cabinet. 5.4 Phone/fax/mailPhones present an interesting avenue for information gathering. You simply find out the phone number of a person or corporate/government department, and then phone up posing as someone (preferably someone not too familiar to the person concerned). In fact, it has been found that the majority of computer hacking incidents not related to company employees get the necessary computer access codes in this way (see below for further details). There is little the individual can do about postal intercepts - so there's not much mileage there. Faxes, in a similar way to phones, can also be useful for getting information, but this tends to be best suited to the forgery of faxes rather than intercepting faxes. 5.5 Social engineering'Social engineering' is the term used to describe the practice of getting information, or creating a response, by making the target consider that something is what it is not. History has shown that such methods are a very effective way of causing trouble. 5.5.1 ImpersonationPhones are lovely impersonal things - you actually have no way of knowing that the person on the other end is who they say they are. You can check the number by dialling 1471 after receiving a call, but dialling 141 before you call prevents this. It is also possible for the person to try and phone you back - but as long as you are careful not to give out a number there is no problem. Results are gained by dominating the conversation by manner, familiarity or the structure of questions, so that the person receiving the call is continually answering your questions rather than putting their own themselves. The simplest way of engineering a phone call is to identify your target, and get to know some detail about their lives, activities and friends. Then you call up their secretary, wife, etc., posing as one of their associates who has forgotten the date and place of a meeting, or the location of a development, or how much money they had to give to the local chief planning officer. With luck, and a lot of verbal bullshit, you can get what you want. Impersonating people in person is very difficult - particularly since most of my friends are hippies and the people we are getting at wear suits. However, with total strangers there are possibilities. Impersonating a police officer is difficult - there are a whole set of mannerisms and structures of vocabulary to master apart from the costume. But little finishing touches like a small scanning receiver in your pocket to give you the traditional chattering police radio talk in your pocket, may help. In practice it is safer to impersonate someone unknown and lowly, but who might hold some sort of power. For example, if you wanted to start a fuss about quarrying, dress as the average shabby construction labourer, and just walk around a village with a theodolite, and get your friend to play along holding a measure. When someone asks what you are doing say that you have come along to measure up for a new opencast coal pit. You could even say that you are conducting a feasibility study for a new six lane bypass next to some posh residences. Impersonating someone lowly can therefore have as much effect as someone who is important. 5.5.2 ForgeryForging letters is very difficult these days, mainly because letters are printed on elaborate coloured paper, with watermarks, etc. However, faxes are monochrome, and have no distinguishing marks. Also fax machines, by the way they scan and transmit the page, destroy much of the quality and effectively mask any slight error in a forger's reproduction. Hence, faxes present the best avenue for forgery. To forge a really good fax you need a computer, an image scanner, a fax machine, and a sample of the standard letter or fax release that your target puts out. You scan all the identifying features of the letter such as letterheads, logos and signatures, and then set these up as images on a page of a desk-top-publisher or wordprocessor. Then, using a typeface of similar style and point size to the real thing, you write your own message. What you do then is up to you. You could just copy the fax using your fax machine, and then stick it up on a noticeboard somewhere. Better still, to make it look as if the fax has been 'leaked' by an employee, reprogram the fax machine with the fax number of the company, make sure you dial 141 to prevent reception of your number, and then fax it to all the local newspapers. 5.5.3 HarassmentSome people consider harassment an acceptable way to campaign - I don't. This is because you can never be sure about only getting the person you are after. For example, many of the animal rights protesters have picketed people's houses - but what about the neighbours who are unconnected with the issue concerned? The only form of harassment I indulge in is swamping businesses with phone call or faxes. This is justifiable because you are attacking a business as an organisation rather than one person in particular, and you can be sure that the action only hits the intended target. There are various ways to do this. If you are just calling by voice you will need to have many tens of people doing it at the same time or BT will intervene for phone harassment. The other option is to send a very long fax. If you have a fax modem this is easy because you create a 60-100 page document on your wordprocessor, and then send it electronically to the fax machine at the other end until you run it out of paper. To do this manually with a normal fax machine is more difficult. Figure 51: Fax loops
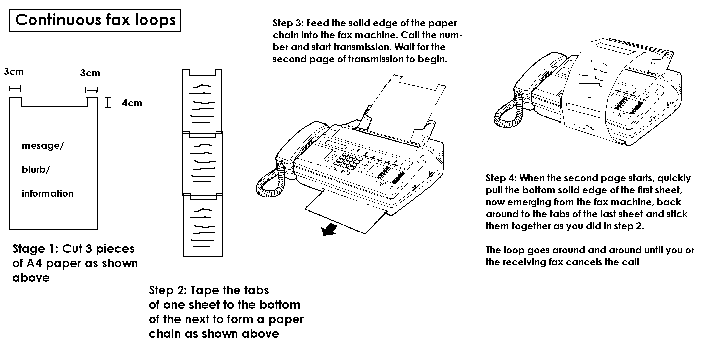 Many modern fax machines are made to disconnect if a page longer than 60cm is sent. Thus, if you made a simple paper loop, the other end would disconnect. The way around this (illustrated below) is to chop chunks out of the end of three sheets of paper, connect them together, and while you are transmitting the first two connect the first sheet to the last. The reason this works is because the paper detector is normally in the centre of the sheet feeder. The gaps in the paper loop are therefore interpreted as a break between pages. However, this system does not work for all fax machines - so you will have to experiment a little with this standard idea. The other option, if you have a fax modem and a lot of numbers, is to get your fax modem to systematically call all the voice numbers and try to send them a fax, over and over again. If there is any comeback from BT there is a simple response... how were you to know there were no fax machines connected to these numbers! 5.6 ComputersComputers, and how to use, abuse and destroy them is a topic in itself. There are many constructive ways to uses computers, there are many destructive ways to use computers, and there are many ways to foul up or damage computers - (generally an axe through the motherboard and hard drive works best). Rather than give an in-depth analysis of how to constructively use or foul up computers, it is easier for the purposes of this handbook to describe what to do if presented with one. This really only applies to desktop or laptop computers. If I got close enough to a desktop computer to do damage to it - I wouldn't. I'd remove it from the site, take it home, after holding it in quarantine at the stash for a few weeks, and extract all the data I could from its hard disk. Computers are generally protected by a password which prevents unauthorised access when you first turn it on. The password is held in an electrical memory, supplied with electricity from a small battery - disconnecting the battery clears the password and allows access. If you take the computer apart, the battery is normally mounted somewhere inaccessible such as under the hard disk. Alternatively, find the CMOS ROM and short the power pins together - this also clears the memory. However, when you've finished with the computer, get rid of it! Sell it on to someone unconnected with sabbing - for cash - or just dump it. Computers and the chips inside them are very valuable, and for this reason they all contain identifying serial numbers. If you get raided and they check the computer, you will be caught. But - how do you do serious harm to a computerised system?... Be aware that not all computers are the friendly looking beasts you see on office desktops in the reception of your local authority. A computer controls the switching of traffic lights; it controls the machinery on many complex industrial processes; it controls the management of the telephone network; it controls the electronics and engine timings in nearly all modern cars. Computers fall into three broad categories: There's not a lot you can do with these systems - straightforward smashing, hammering and cutting is the best options. If you don't have a lot of time, just remove some of the larger circuit boards, place them between two blocks lean them against the wall, and stamp in the middle to snap it in two. PLC's are identifiable because they normally have small keypads and LCD/LED dot matrix displays. Hardwired units are essentially small circuit-board based computers that control specific small scale tasks, and are not programmable. A good example are automatic washing machines, or a video recorder. In terms of extracting information these systems are worthless, but there are a number of alternative options... The whole subject of using computers will be covered in depth in Volume III of this series.
[Back to Contents]
[Go to next section]
|